
Can Generative AI be used unsupervised?
Generally speaking, we have come to expect computers to not make arithmetic mistakes. Can doing simple arithmetic be considered to be a part of Language?


Generally speaking, we have come to expect computers to not make arithmetic mistakes. Can doing simple arithmetic be considered to be a part of Language?

Much has been said about vulnerability prioritization by different cybersecurity vendors, but the absence of a standard guide from an authoritative source had left much

Cybersecurity landscape is laden with myths and misconceptions. In this article we will look at top 5 myths for a good “reality check”. Myth #1 –
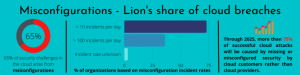
Given that misconfigurations contribute to a fair share of cloud breaches, it is vital to keep tab on your cloud environments. Cloud environments are rarely

The 5G revolution is making waves and headway. 5G promises ultrafast speeds and reduced lag time (latency) along with massive bandwidth and ability to connect
A cyber risk score provides an objective framework for the evaluation of a security posture. By converting these evaluations into an easy-to-grasp representation of qualitative cyber