
Zero-trust, continuous, automated protection for your container images and apps and K8S environments
Zero trust discovery unlike other container security solutions. By using our simple, python based, open source twigs script for discovering your containers, which runs in your own network, you can be sure that your precious container images or credentials to access them are never shared with ThreatWorx.
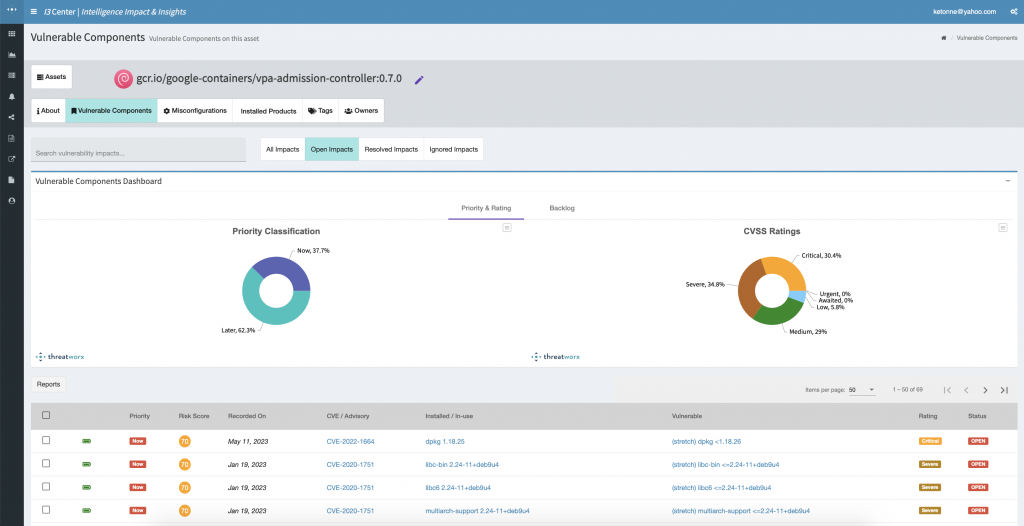
Prioritize based on signals delivered by our AI powered threat and vulnerability intelligence to identify the most critical vulns early for remediation.
Integrate your enterprise Docker, ECR, ACR, GCR or repositories and K8S clusters for complete automation. Use our real time alerts, webhooks and ReST API and integrations with Slack, MS Teams for remediations and downstream workflows.
Simple, flat pricing, not tied to number of developers, number of images, number or repositories or scans.
Stop looking for point solutions. When you are ready, ThreatWorx will easily address your other proactive security requirements for code, cloud and more.



Flexible options to integrate the platform with a wide variety of point solutions for discovery of your attack surface as well as for remediations and other tooling. Use our powerful ReST API and our native Webhooks to build your own workflows.