ThreatWorx Attenu8 – Vulnerability Prioritization aligned with CISA SSVC

Much has been said about vulnerability prioritization by different cybersecurity vendors, but the absence of a standard guide from an authoritative source had left much to be desired. Well that wait of now over, Cybersecurity and Infrastructure Security Agency (CISA) recently published the CISA Stakeholder-Specific Vulnerability Categorization (SSVC) guide. It is basically a customized decision tree […]
Top 5 cybersecurity myths busted!

Cybersecurity landscape is laden with myths and misconceptions. In this article we will look at top 5 myths for a good “reality check”. Myth #1 – Poor proactive security is acceptable as long as you have good reactive cybersecurity. Reality #1 – Good focus on proactive cybersecurity ensures good cybersecurity posture for the organization. Sadly this is […]
Keeping tab on your cloud environments
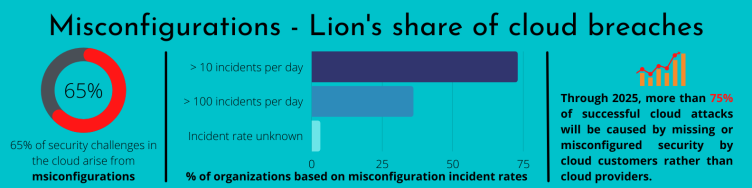
Given that misconfigurations contribute to a fair share of cloud breaches, it is vital to keep tab on your cloud environments. Cloud environments are rarely static, especially given that most of us leverage cloud for the elasticity and flexibility it provides. Logging and monitoring provides an easy way to get insights into your ever changing […]
Security Guidance for 5G Cloud Infrastructures from NSA & CISA

The 5G revolution is making waves and headway. 5G promises ultrafast speeds and reduced lag time (latency) along with massive bandwidth and ability to connect lot more devices. Cloudification is key for the success of 5G. What is Cloudification? Cloudification is enabling network operators to innovate new and enhanced services and respond to market demands with the scalability […]
Learnings from CISA Ransomware Guide

CISA released Ransomware Guide last year. I found it to be very informative and hence thought of sharing the gist of learnings from the CISA Ransomware Guide. Before I dive into the learnings from the guide, I want to highlight CISA tag line: Defend Today, Secure Tomorrow This makes perfect sense with focus on “proactive cybersecurity for […]
Is Security factored in your Digital Transformation journey?

Around 3 years back, many companies embarked on their digital transformation journey. Others were forced into it later with the pandemic. Pandemic pushed companies to move ahead on their digital transformation journey at breakneck speed. Many organizations jumped on the digital transformation bandwagon without much thought about how to bring security in the picture. How […]
Beyond risk-based cybersecurity…

A 2019 article from McKinsey titled “The Risk-based Approach to Cybersecurity” talked about the need for organizations to move from a “maturity-based” to a “risk-based” approach to cybersecurity. First let us get clarity on some definitions from that article here. Cyber risk is just another kind of operational risk and cyber risk is not the same as cyber threat. […]
How cyber insurance can incentivize cyber security?

In the previous article, we saw how taking a Proactive Approach to Cyber Security is key and how it relates to Cyber Insurance. In this article we will see how cyber insurance can incentivize better cyber security practices amongst policy holders. RUSI (Royal United Services Institute) for Defense and Security Studies published a paper titled “Cyber Insurance […]
Cloud Security Simplified!
According to Gartner, pandemic-induced surge in public cloud spend is predicted to run until 2024 (reference: ComputerWeekly). This increase is fueled by organizations wanting to conserve cash, optimize IT costs and support & secure a remote workforce and ensure resiliency. Increased cloud footprint translates to an increased attack surface for most organizations. Cyber attacks on cloud […]
Cyber Insurance and Proactive Security: Not an either or proposition.

Earlier last month, CNA Financial reportedly paid a $40 million ransom after a ransomware attack and the CEO of Colonial Pipeline Co. admitted that his firm paid $4.4 million to a criminal gang after a ransomware attack led the company to shut down its 5,500 mile-long pipeline for nearly a week. It’s not clear whether Colonial Pipeline and CNA […]
