
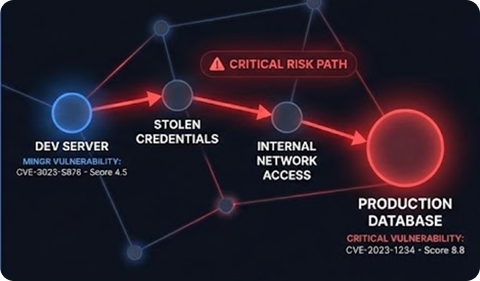
Attackers typically use a series of vulnerabilities and exploits to move laterally within your network. Vulnerability scans reports do not highlight these chains very effectively.
A fraction of the threats and vulnerabilities affecting your attack surface will have the right ingredients for attackers to move from one system to another. Finding and prioritizing such threats is important but difficult using current solutions.
The size and scale of today’s enterprise attack surface makes this a needle-in-the- haystack problem. Without the right solution to visualize these paths they will likely never be prioritized for remediations.
Use ThreatWorx’ advanced universal scanner to identify vulnerabilities, malware exposure and potential points of entry for attackers in your external and internal attack surface.
See the blast radius of individual threats and the opportunities for lateral movements from external endpoints to your crown jewel services using our integration with Rocketgraph.
Identify all dangerous paths leading to your crown jewel services and prioritize remediation of vulnerabilities and threats in that path. Reduce the opportunities for lateral movements.